3rd Party Risk Management , General Data Protection Regulation (GDPR) , Governance & Risk Management
What Apps Are Peeking Into Your Gmail?
Google Responds To Investigation Into Email Scanning By Third-Party Apps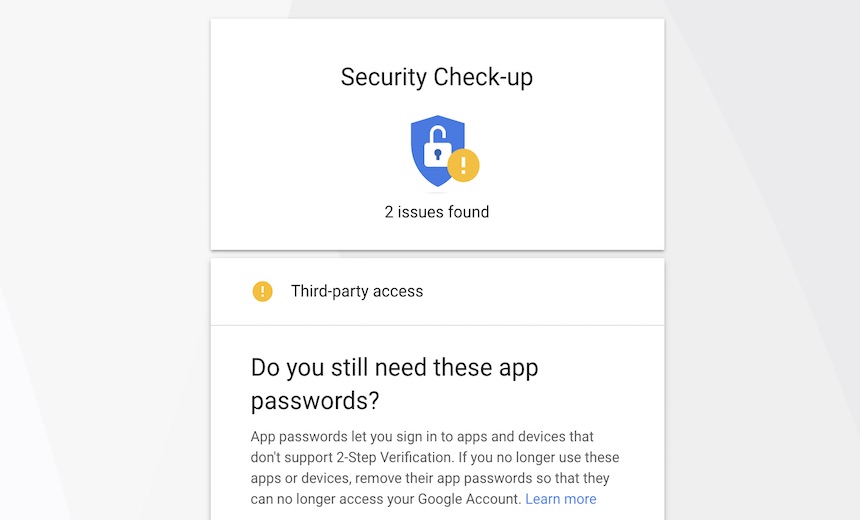
Google has responded into an investigation of third-party applications that scan email inboxes to gather marketing data, saying it closely vets apps and suspends ones that do not meet its standards.
See Also: Modernize with Monitoring: Keys to Third-Party Risk Management Success
The response comes after a Wall Street Journal investigation that found marketing companies that performed automated scans on email inboxes, and, occasionally, had human reviewers analyzing and reading emails.
The investigation contended that the marketing companies, Return Path and Edison, did not specifically inform users their emails may be read. But the companies maintain their user agreements were sufficient disclosure, the Journal reports.
"Trackers, forced redirections and malvertising in general are issues that can have far more impact on users and need to be addressed as well."
—Suzanne Frey, Google
Google allows third-party applications, such as trip planners, calendars and CRM systems, to add extra functionality within email. Those applications may have carte blanche access to see all emails.
But the company says third-party applications are vetted to ensure they're transparent with users over how the data is used and to ensure the apps aren't asking for too many permissions, Google says.
"We review non-Google applications to make sure they continue to meet our policies and suspend them when we are aware they do not," writes Suzanne Frey director of Security, Trust, and Privacy for Google Cloud, in a blog post.
But the Journal's investigation contends that Google does little to police outside developers, which analyze an astounding amount of email while essentially self-supervising.
Email Scanning
Those in the information security community have long known the danger of adding third-party apps with email access. Attackers have been known to create bogus applications in order to gain access to email, misrepresenting the permissions of the app.
Granting access just takes one click. The attacker then gains a persistent access token to the victim's account. That access persists even if a person changes their password (see Phishing Defense: Block OAuth Token Attacks).
Google, Microsoft and other cloud-services providers have security panels that show other apps linked to an account. But people may only check the panels rarely and neglect to revoke apps no longer needed.
Frey writes "before a non-Google app is able to access your data, we show a permissions screen that clearly shows the types of data the app can access and how it can use that data."
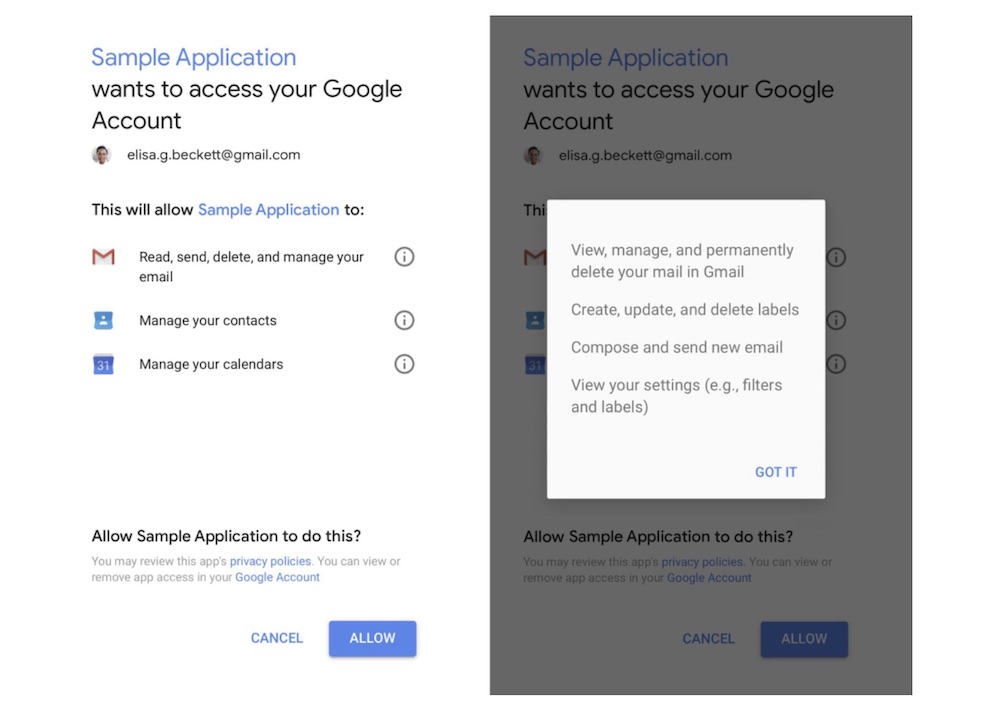
Clear disclosure to consumers is a central part of Europe's General Data Protection Regulation, which went into effect on May 25. The regulation is the strictest one in the world, requiring companies to disclose collected data on request, delete it on request and write clear data use policies.
Google advises that users should check the Security Checkup feature, which displays which third-party apps are connected to an account. For organizations running Google's G Suite, admins have more powerful tools to prevent users from connecting other apps to accounts.
"G Suite admins can control the scopes of data users are able to grant non-Google apps access to by whitelisting connected OAuth apps," Frey writes. "This ensures that G Suite users can give access only to non-Google OAuth apps that have been vetted and are trusted by their organization."
Beware: Humans Involved
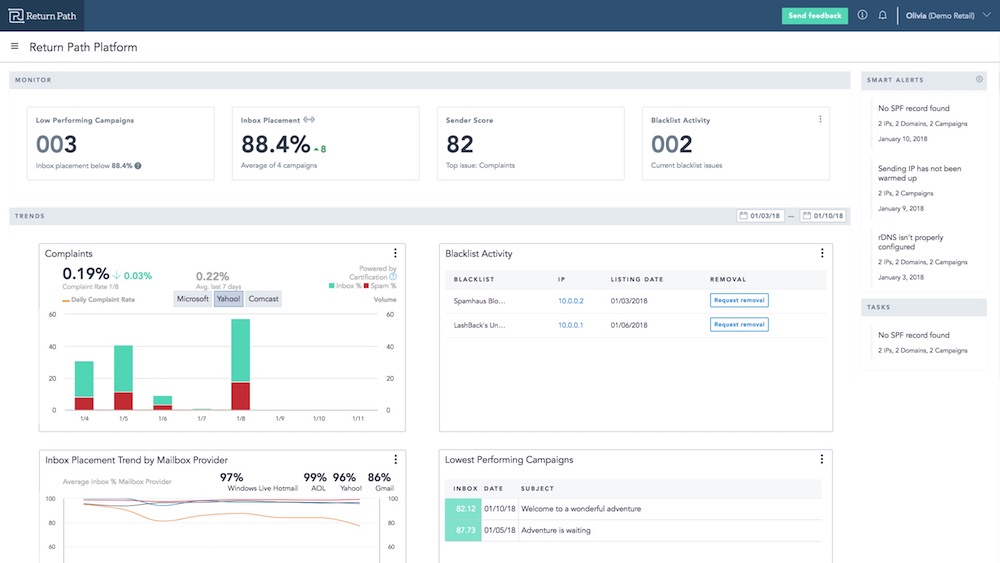
Return Path, a company that specializes in fine-tuning marketing message based on whether emails have been read, was scanning as many as 100 million email messages a day, the Journal reports.
But humans were also reading email. The Journal reported that Return Path employees read 8,000 emails two years ago in order to train the company's software. The action was taken after Return Path's email scanning software was flagging personal emails as commercial ones.
Another company, Edison Software, which makes a Gmail app, also manually reviewed hundreds of emails it had access to for a new feature, the Journal reports. The publication writes there are no indications that either Edison or Return Path abused information.
Although users have to grant access to third-party apps, there are concerns whether users fully grasp that power that is handed over.
There are many e-mail reading apps that vie for the access. Return Path offers it owns app, and there are 163 others from its partners that also have the ability, the Journal reports. Third-party email apps in Apple's Store for iOS and Android number 379.
Return Path's platform for marketers allows them to see whether commercial emails are read. Screenshots of emails can be seen, although the name and addresses are removed, the Journal reports.



















