Breach Notification , Data Loss Prevention (DLP) , Governance & Risk Management
PageUp Breach: Personal Data Exposed
HR Software Provider Says Names, Addresses, Emails and Phone Numbers Exposed
Human resources software developer PageUp is warning that malware-wielding attackers may have accessed a raft of personal data stored in the company's systems.
See Also: The Path to Data: Identities are the Keys, Apps are the Gateway
The Australian company, which has 2 million customers - including many large companies and organizations worldwide - disclosed on June 5 that it had detected unauthorized activity on its systems (see HR Service Provider PageUp Discloses Data Breach).
Digital forensic experts have concluded that the accessed data may have included names, addresses, email addresses and phone numbers, writes PageUp CEO Karen Cariss in a Tuesday update. She did not specify how many records may have been viewed.
"While investigations continue, on the balance of probabilities, we believe certain personal data relating to our clients, placement agencies, applicants, references and our employees has been accessed," Cariss writes.
Some usernames and passwords were exposed, she says. However, the passwords were hashed using bcrypt and also salted, which refers to a security step that makes hashed passwords harder to crack.
The exposure of authentication credentials "is considered to be of very low risk to individuals," Cariss writes. PageUp has nonetheless recommended that all users reset their passwords.
Not Back To Business
The breach may be the largest one since Australia's mandatory data breach notification law went into effect on Feb. 22. The law requires companies to notify regulators and affected customers within 30 days.
PageUp said in its initial disclosure that malware has been removed from its systems. Several companies, including Australia Post, Telstra and the grocery chain Coles, suspended their connections to PageUp's systems while its mitigation efforts continued.
As of Monday, PageUp application systems at Coles, Telstra, Australia Post and Commonwealth Bank remained offline due to the incident.
"While investigations continue, on the balance of probabilities, we believe certain personal data relating to our clients, placement agencies, applicants, references and our employees has been accessed."
—Karen Cariss, PageUp CEO
PageUp's data segregation practices may have prevented the breach from becoming more damaging.
Cariss reiterated on Monday that "the most critical data categories including resumes, financial information, Australian tax file numbers, employee performance reports and employment contracts are not affected in this incident."
Also, no information was accessed from its various HR software modules, which include services for onboarding employees, performance management, learning, compensation and succession.
Cariss writes that several independent cybersecurity firms are working on the breach investigation, along with the Australian Cyber Security Centre and Australian Federal Police.
The Office of the Australian Information Commissioner has been in contact with PageUp. The OAIC can levy fines up to AU$360,000 (US$274,000) for individuals and $1.8 million for organizations for failing to report a breach.
Ready for GDPR
PageUp recently described its path to become compliant with Europe's General Data Protection Regulation (see Europe's Strong GDPR Privacy Rules Go Into Full Effect).
The company set up an internal working group more than a year before the regulation was scheduled to take effect, writes David Clarke, PageUp's ISO compliance and security officer.
"Being a talent management solution, collecting and analyzing personal data is what we do," Clarke wrote in a May 14 blog post. "In some respects, our industry is one of the toughest for GDPR."
Clarke said that PageUp already had an audited Information Security Management System in place, which "meant that the majority of the items that are called out in the GDPR (from a security side) were already being addressed."
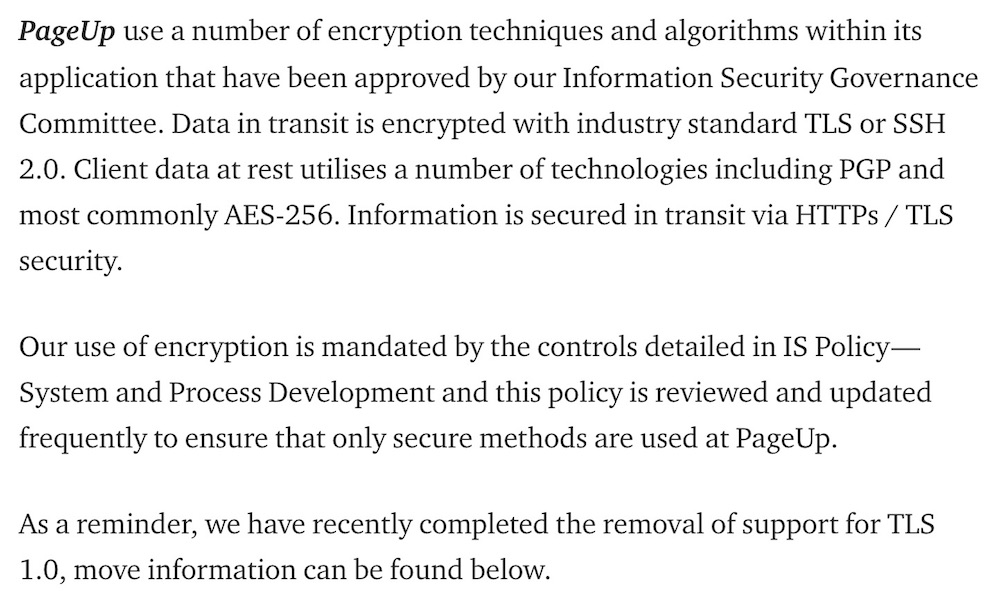
In light of GDPR, PageUp also modified its data protection framework, which dictates what the company can do with certain types of information and other processing and encryption requirements. The framework covers client personal information, confidential information, client data, metadata and public domain data, Clarke said.
Clarke said the company uses "a number" of encryption techniques. Data at rest - which is presumably what was compromised - is encrypted with technology that includes PGP and most commonly AES-256, he said.





















